
Reverse Engineering Using Radare2 - Part 2
21 December 2017
By Jacob Pimental
This article is a continuation of my first article “Reverse Engineering Using Radare2” where I gave a basic introduction to the tool. I highly suggest starting there if you haven’t already, as it covers the very basics.
This article will demonstrate some of the other interesting features of Radare2 by walking you through how to solve a simple Capture the Flag style program. You can download this program on my gitHub (the crackme binary). If you go ahead and run this program you’ll see that it requires us to input a password.
$ ./crackme
What's the password?
If we try to give it a password that we know is wrong, we’ll see that we get a message denoting our failure.
$ ./crackme
What's the password? test
You failed
$
There are multiple ways we can approach this problem. We can attempt to bruteforce the password, sending the program a bunch of different letter combinations until we eventually figure out the password. The standard password length is around 8 characters. We can safely assume that the password is comprised of upper and lowercase letters, and maybe even numbers. According to this calculator, then it would take us about 15 years to bruteforce the password. I don’t have that long to wait, so we’re going to use Radare2 to crack the password.
Just like in the last tutorial we start by using rabin2 to get some basic information about the program. Let’s run it with the -I flag and see what we’re dealing with.
$ rabin2 -I crackme
arch x86
binsz 6759
bintype elf
bits 64
canary true
class ELF64
crypto false
endian little
havecode true
intrp /lib64/ld-linux-x86-64.so.2
lang c
linenum true
lsyms true
machine AMD x86-64 architecture
maxopsz 16
minopsz 1
nx true
os linux
pcalign 0
pic true
relocs true
relro partial
rpath NONE
static false
stripped false
subsys linux
va true
$
Just like last time it looks like we have an x64 Linux Binary that was written in C. This information is interesting, but doesn’t really help us figure out what the password is. Maybe the strings in the binary will give us a clue. We can view them using rabin2. Normally we use the normal -z flag, but that shows a lot of output. We can use the -zqq flag to show just the strings.
$ rabin2 -zqq crackme
What's the password?
radare2
Congratulations
What's the second password?
What's the third password?
You failed
Flag is: r2{%s %s %s}\n
$
We can see a lot of interesting things here! We see the message that says “You failed”, which we got when we got the password wrong. We can also see the string “Congratulations”, which we can assume we get when we get the password right. We also see the string “radare2”. We can assume that that may be the password. We may be wrong but it never hurts to check.
[jacob@jacob-pc Blog]$ ./crackme
What's the password? radare2
Congratulations
What's the second password?
Great! We got the password! Sometimes it isn’t this easy, the password string could be obfuscated or encrypted. We would have to reverse the encryption in a case like that, but we seem to be lucky this time. It looks like we need to input another password to solve this challenge. I didn’t see anything else that looks like a password when we checked the strings, so we’re going to have to dig deeper than that. Let’s load up the binary in radare2 and analyze it using “aaa”. This analyzes all of the functions the program may have.
$ r2 crackme
-- Run your own r2 scripts in awk using the r2awk program.
[0x000006f0]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze len bytes of instructions for references (aar)
[x] Analyze function calls (aac)
[x] Use -AA or aaaa to perform additional experimental analysis.
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[0x000006f0]>
We should also seek to the main function, as that is where the program starts.
[0x000006f0]> s main
[0x000007fa]>
Now that we’re at the main function we’re going to switch into radare2’s graph mode. This will help us see how the program flows and see where the checks for these passwords are being done at. To go into graph mode use the command “VV”.
[0x000007fa]> VV
You should now be seeing radare2’s ascii graph. You can navigate the graph using HJKL keys like in Vim, or the arrow keys. If you take a look at the first block in the graph you can see the check for our first password.
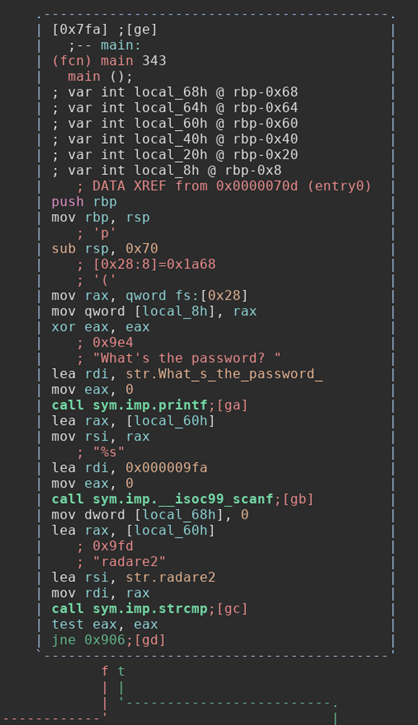
You can see in the last few lines that it is taking the string “radare2” and comparing it to the users input using the function strcmp. Then it checks to see if the strings are equal or not. If they are not equal then we follow that green T line (which stands for true) down to these blocks of code:
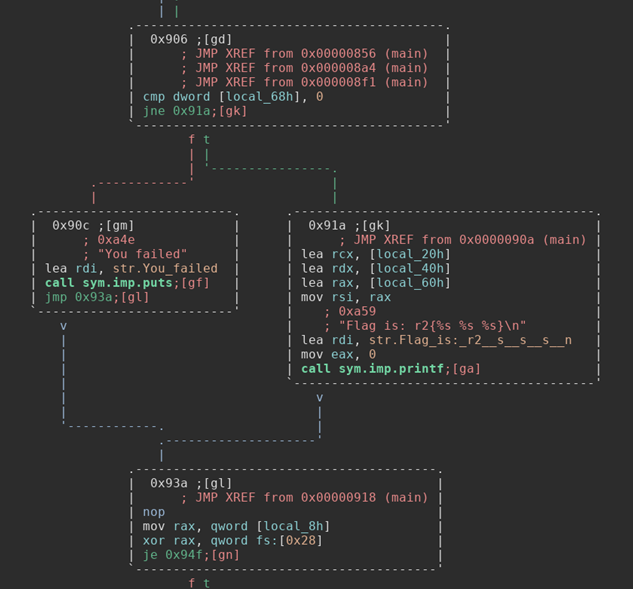
We can see in the top block that the program is comparing some variable to zero. If it is not equal to zero then it prints out the statement “Flag is: r2{%s %s %s}”. This must be our flag for completing the challenge. Unfortunately it uses format strings to format what is in the flag, so we don’t know what the flag is just by looking at the string. If that variable in the first block is equal to zero then it prints out the “You failed” message. So we can gather from this that some variable that dictates whether or not we get the flag is changed once we get all the passwords correct. Let’s go up to the top and see what happens if we get that first password correct.
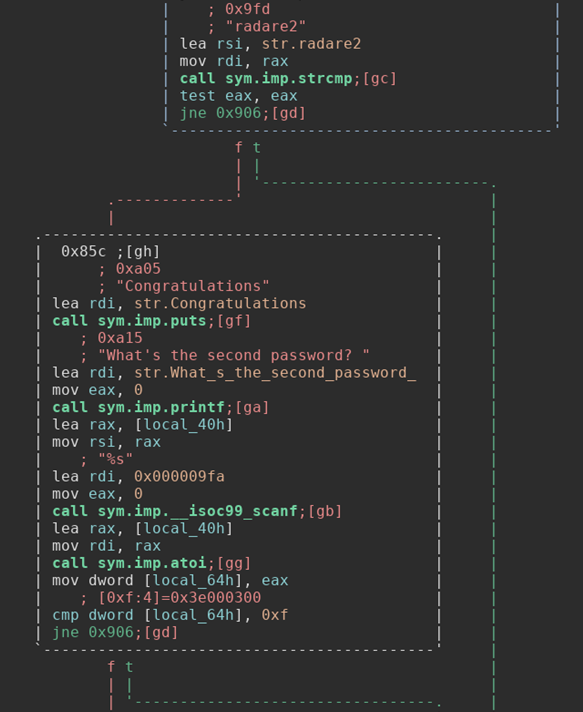
So it prints out the “Congratulations” string and then prints “What’s the second password?”. It then grabs our input using scanf and runs that through the function atoi. The atoi function is used to convert a string into an integer. So the second password must be a number! We can see that it is comparing the output of atoi to the value 0xf. Now, if you don’t know hexadecimal offhand then radare2 has yet another great tool for you! Open a new terminal and use the command “rax2” to convert the value 0xf into an integer.
$ rax2 0xf
15
$
So the second password is 15! Let’s try that and see if it works.
$ ./crackme
What's the password? radare2
Congratulations
What's the second password? 15
Congratulations
What's the third password?
It looks like it requires us to put in a third password. Let’s move down to the next block of code in radare2 and see what we need to do.

This looks very similar to the last password check it did. We can see that it asks for the third password, runs the user’s input through atoi and compares that to the hex value 0x539. If we run that through rax2 we find that the decimal equivalent of that is 1337. So we plug that in as the last password and we get:
What's the third password? 1337
Congratulations
Flag is: r2{radare2 15 1337}
$
Great! It gave us our flag! If this was an actual Capture the Flag then we could plug this in somewhere for points.
We managed to get the passwords without having to run the program multiple times and without having to guess the password at all. By reverse engineering the application it was like the program was just handing us the information we needed. Reverse engineering is a very handy tool to have in any setting as you can use it to find out everything an application is doing. I hope this introduction to radare2 was helpful to those wanting to get started in the field. You can follow me on Twitter or LinkedIn if you need any more help or guidance!
Thanks for reading and happy reversing!






