
Flare-On 5: MineSweeper Write-up
13 October 2018
By Jacob Pimental
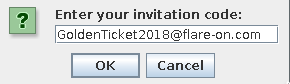
With the Flare-On 5 challenge over and done I thought it would be a good idea to present my solutions for the challenges I managed to solve. This post will group the first two challenges together since they follow the same “story”, the Minesweeper World Championship is coming soon and you weren’t invited. However, you somehow managed to get your hands on the registration application for the challenge and need to crack the code in order to register. Let’s take a look at this application and see what we are dealing with.
Upon unzipping the 7z file we are greeted with a .jar application. A jar file is basically the same as a regular zip folder, so we will unzip it and get the class files.
$ unzip MinesweeperChampionshipRegistration.jar
Archive: MinesweeperChampionshipRegistration.jar
inflating: META-INF/MANIFEST.MF
inflating: InviteValidator.class
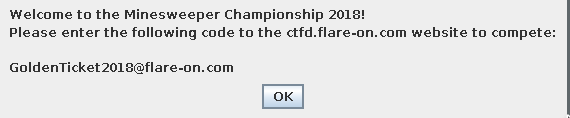
Unzipping the archive reveals the file “InviteValidator.class”. This most likely contains the main method for the java application. Running strings on it reveals the flag:
$ strings InviteValidator.class
...
GoldenTicket2018@flare-on.com
...
That was a relatively painless challenge. The second challenge is the actual Minesweeper competition that we have to beat. Running the binary through rabin2 -I reveals one very important aspect about this challenge, it’s .NET.
$ rabin2 -I UltimateMinesweeper.exe
Metadata Signature: 0x1aa8 0x10001424a5342 12
.NET Version: v4.0.30319
...

If would hadn’t guessed it, I really don’t enjoy reversing .NET applications. It forces me out of my comfortable Linux environment and makes all of my tools obsolete. We need to move this over to a Windows environment in order to solve the challenge. When you run this application you can see that it looks like your normal MineSweeper game.
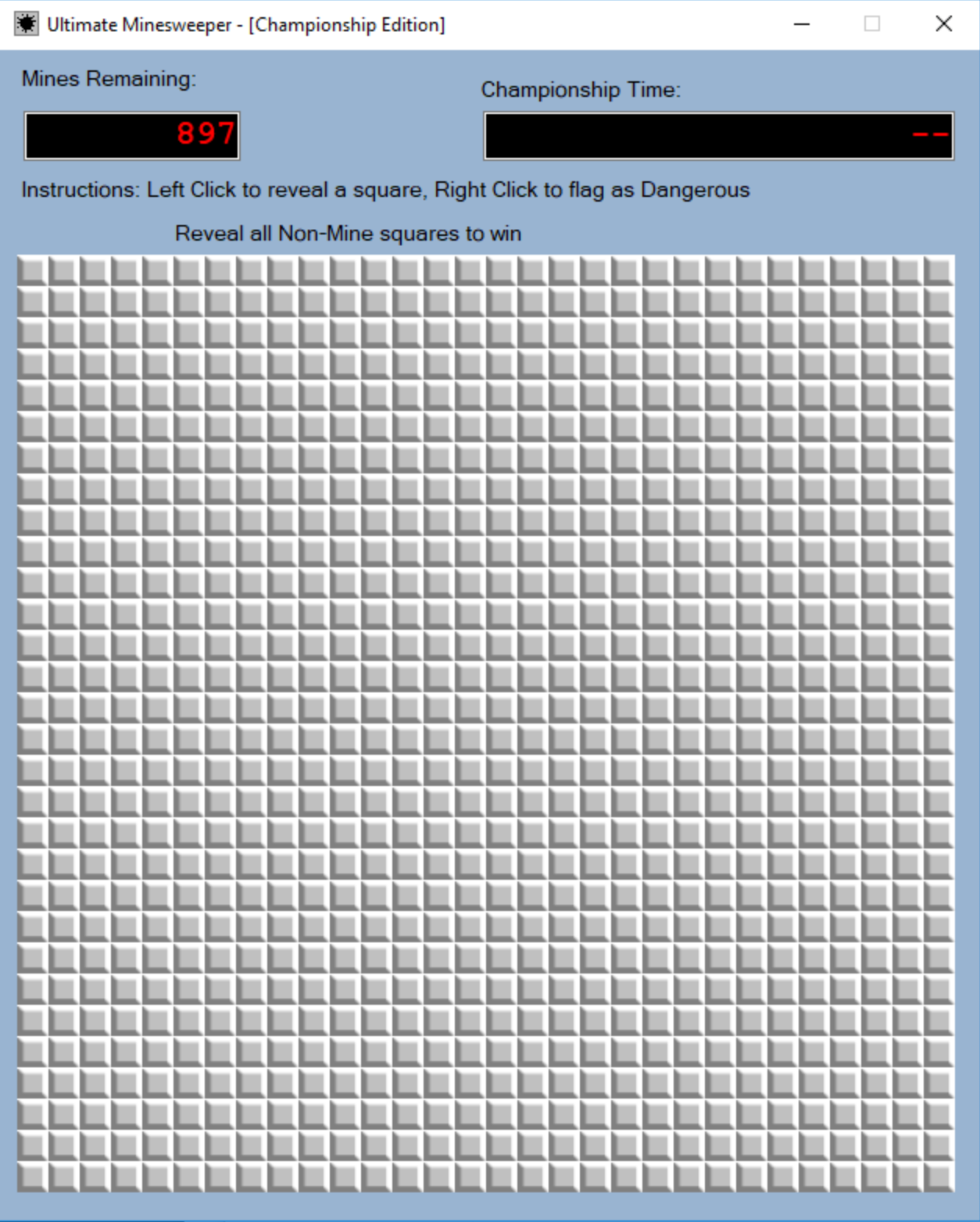
The only difference is that there are 897 mines we have to uncover. While it would be really fun to sit there trying to beat the game the normal way, we can just as easily cheat using reverse engineering! I’m going to show you a tool I use for .NET applications called DnSpy. This is a .NET decompiler and debugger that also allows you to change the application’s code and recompile it. This feature might come in handy when solving this challenge. In DnSpy you can see that we have a MineField class and a MineFieldControl class. The MineFieldControl class contains the function MineFieldControl_MouseClick, which handles the event when the user clicks on one of the squares.
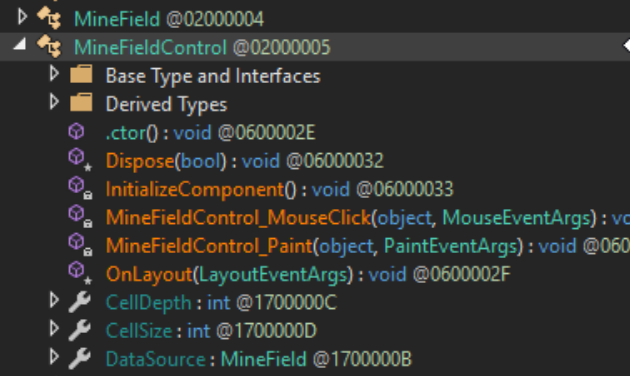
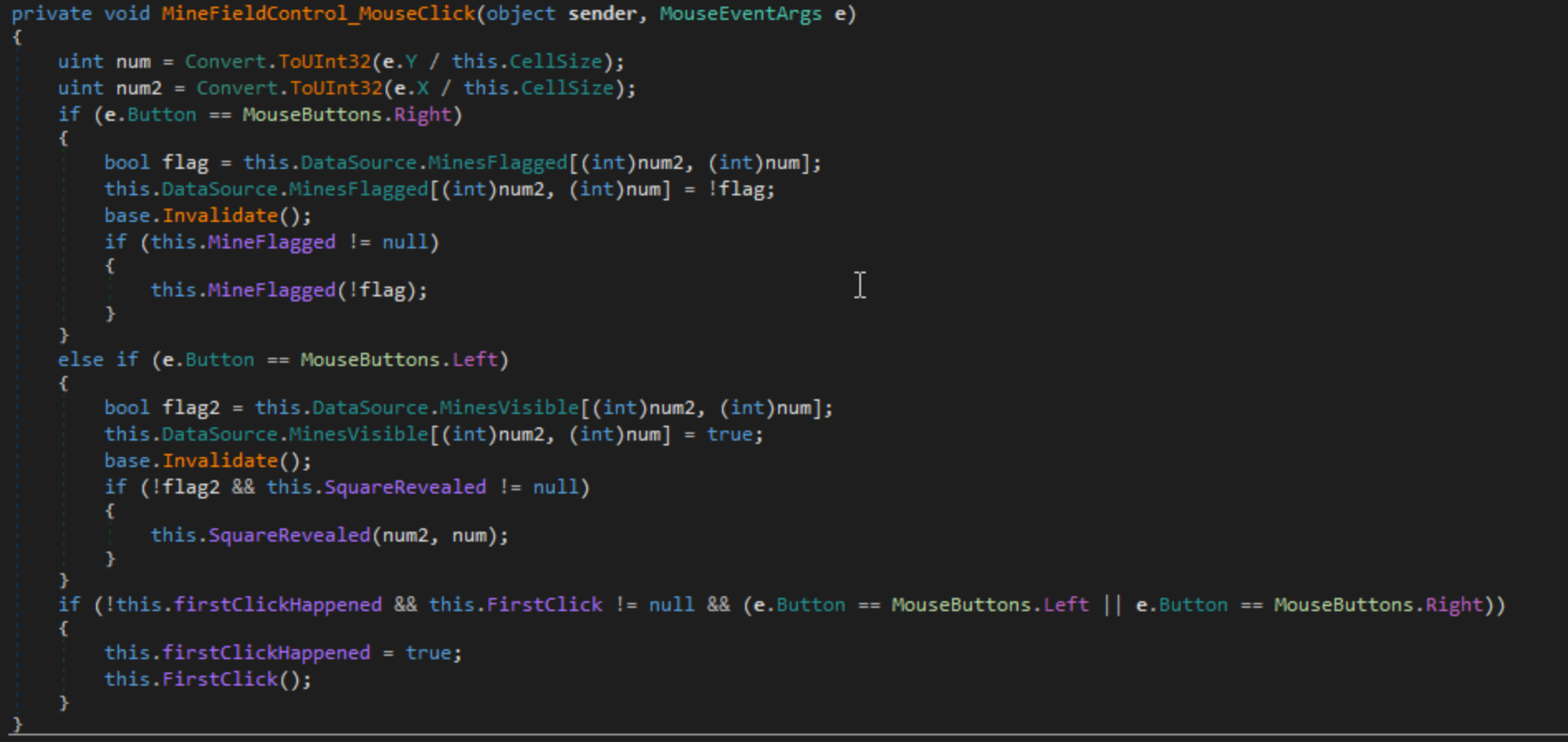
We can take advantage of this function, changing it’s behavior however we want. You can change a block of code in DnSpy by right clicking the code and selecting “Edit Method”. I decided to have it loop through every square on the board and flag it if the square contains a mine and reveal it if the square does not. I changed the MouseButtons.Right If Statement to look like this:
if (e.Button == MouseButtons.Right)
{
bool flag = this.DataSource.MinesFlagged[(int)num2, (int)num];
this.DataSource.MinesFlagged[(int)num2, (int)num] = !flag;
base.Invalidate();
int x = 0;
while ((long)x < (long)((ulong)this.DataSource.Size))
{
int y = 0;
while ((long)y < (long)((ulong)this.DataSource.Size))
{
if (this.DataSource.MinesPresent[x, y])
{
this.DataSource.MinesFlagged[x, y] = true;
this.MineFlagged(true);
base.Invalidate();
}
else
{
this.DataSource.MinesVisible[x, y] = true;
base.Invalidate();
this.SquareRevealed((uint)x, (uint)y);
}
y++;
}
x++;
}
}
This code loops though every square on the board when the user presses the Right Mouse Button. If the square contains a mine, dictated by the DataSource.MinesPresent variable, then it will flag the mine using the MinesFlagged variable and the MineFlagged function. If the square is not a mine then it sets the MinesVisible flag to true and calls the SquareRevealed function. Now if we hit recompile you can see that our code is changed.
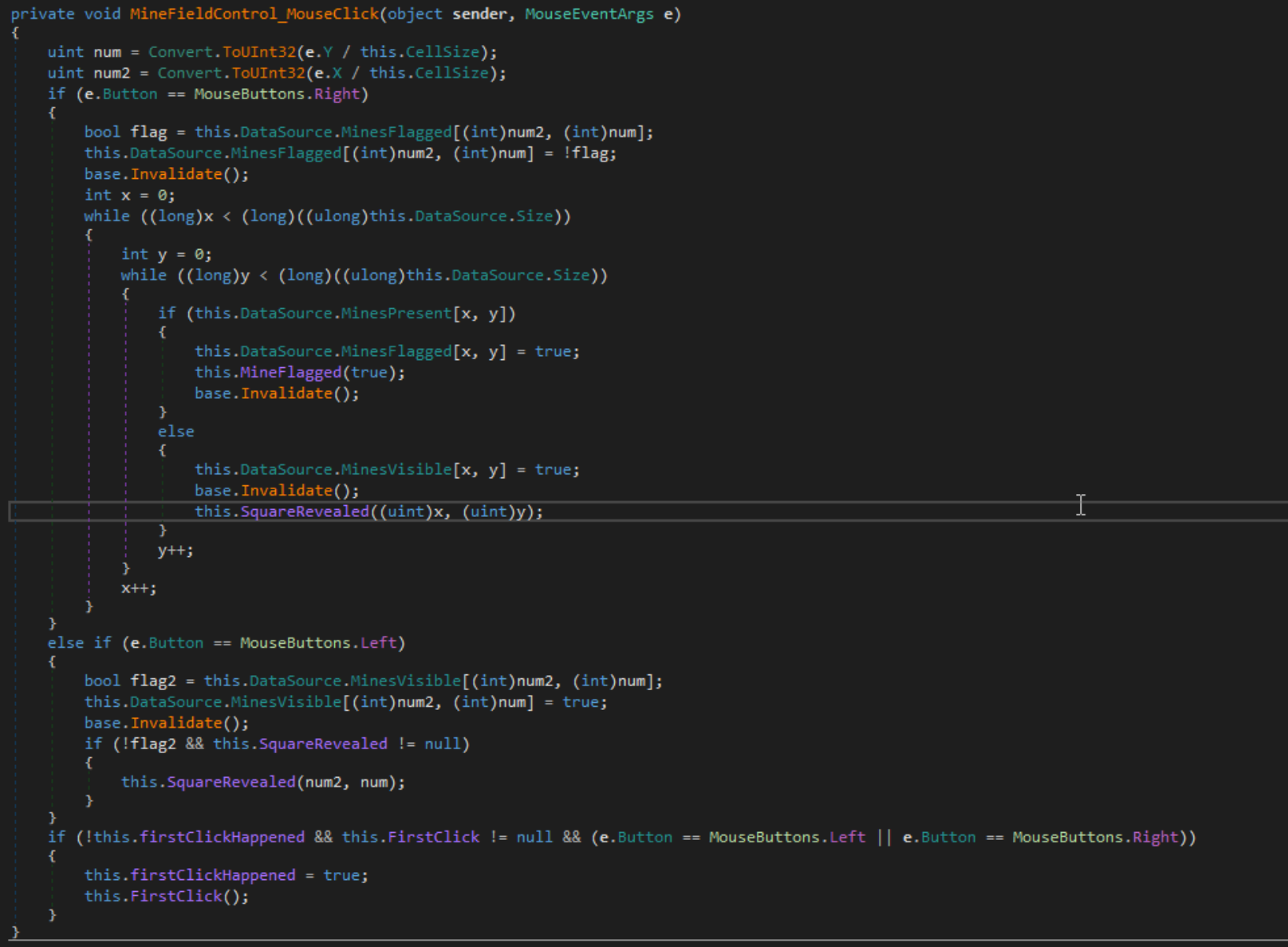
Now if we save the newly compiled program (Ctrl+Shift+S), rerun it and right-click any square we will win the challenge.
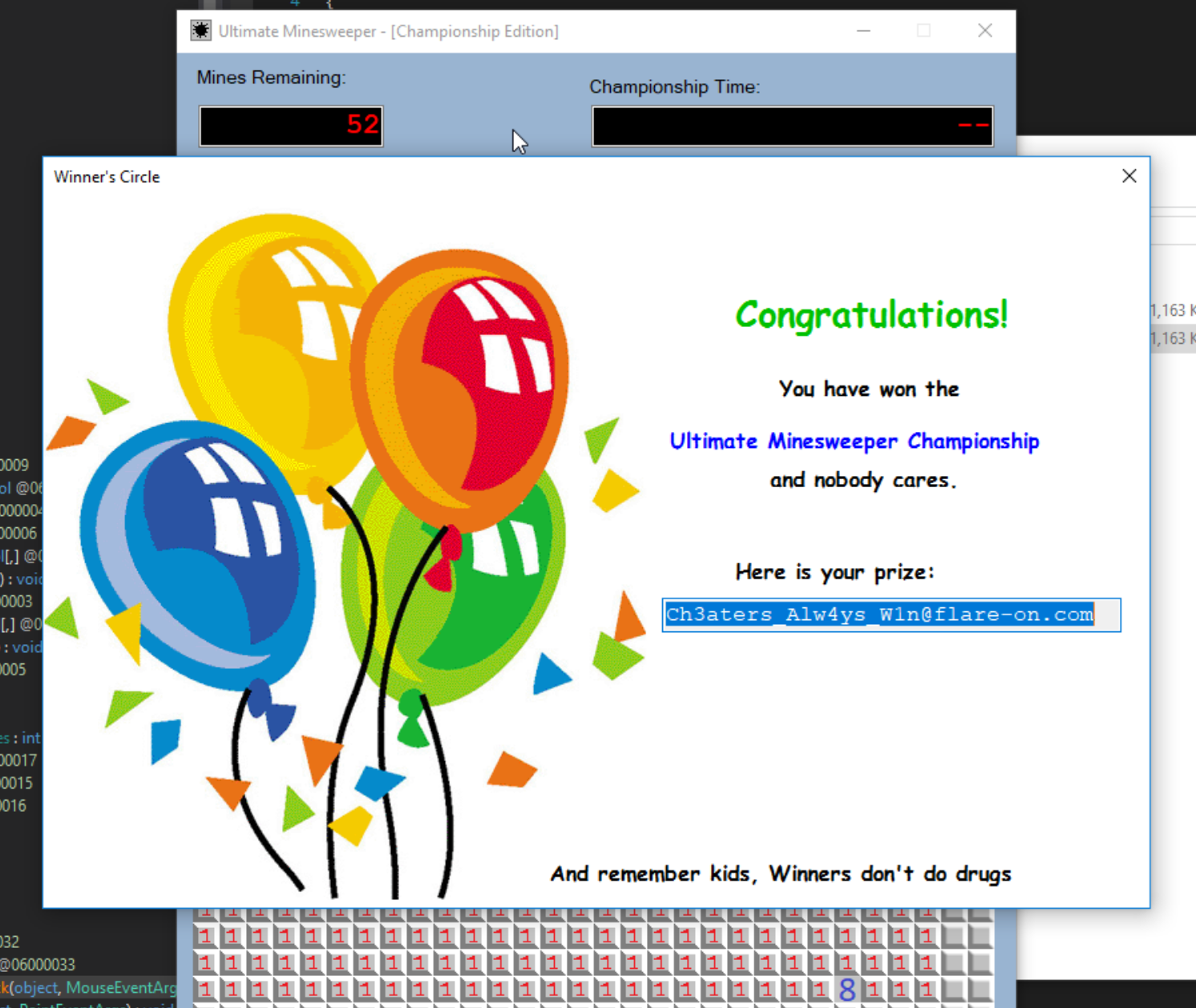
The flag is Ch3aters_Alw4ys_W1n@flare-on.com. These challenges weren’t too difficult, but were a fun introduction to the rest of the Flare-On challenges. I really enjoyed the story behind the challenge and learning the DnSpy tool. In my next post I will document how I solved the FLEGGO challenge, which involves r2pipe and some python scripting! If you have any questions or comments about this article feel free to reach out to me on Twitter or LinkedIn. Criticism is always welcome!
Thanks for reading and happy reversing!






